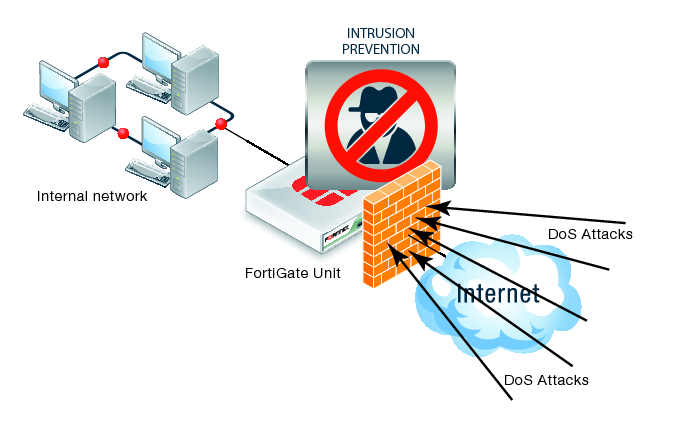
DOS Attacks
How To Identify Fake Facebook Accounts
July 20, 2014
Botnets
July 20, 2014Denial of service (DOS) attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. Many DoS attacks, such as the Ping of Death and Teardrop attacks, exploit limitations in the TCP/IP protocols.
Types:
Teardrop attack is type of attack where fragmented packets are forged to overlap each other when the receiving host tries to reassemble them.
Ping of death type of DoS attack in which the attacker sends a ping request that is larger than 65,536 bytes, which is the maximum size that IP allows. While a ping larger than 65,536 bytes is too large to fit in one packet that can be transmitted, TCP/IP allows a packet to be fragmented, essentially splitting the packet into smaller segments that are eventually reassembled. Attacks took advantage of this flaw by fragmenting packets that when received would total more than the allowed number of bytes and would effectively cause a buffer overload on the operating system at the receiving end, crashing the system. Ping of death attacks are rare today as most operating systems have been fixed to prevent this type of attack from occurring.
DDOS Attack: A distributed denial of service attack (DDoS) occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. This is the result of multiple compromised systems (for example a botnet) flooding the targeted system(s) with traffic. When a server is overloaded with connections, new connections can no longer be accepted.
Peer to Peer Attack Attackers have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks. Peer-to-peer attacks are different from regular botnet-based attacks. With peer-to-peer there is no botnet and the attacker does not have to communicate with the clients it subverts. Instead, the attacker acts as a “puppet master,” instructing clients of large peer-to-peer file sharing hubs to disconnect from their peer-to-peer network and to connect to the victim’s website instead. As a result, several thousand computers may aggressively try to connect to a target website. While peer-to-peer attacks are easy to identify with signatures, the large number of IP addresses that need to be blocked (often over 250,000 during the course of a large-scale attack) means that this type of attack can overwhelm mitigation defenses.
For all known DOS attacks, there are software fixes that system administrators can install to limit the damage caused by the attacks.